Electronic Warfare AKA Electromagnetic Warfare
According to the EW doctrine it can be divided into three major subfields:
-
Electronic Support (ES): is the branch of the Electronic Warfare (EW) domain with the task of immediately recognizing threats present in the environment by detecting, classifying, recording, identifying and locating radio frequency (RF) band emitters of surveillance and communication links of military systems hostile.
ES systems are passive equipment, i.e. they do not radiate (they remain electronically silent during their operation). -
Electronic Attack (EA): is the branch of the Electronic Warfare (EW) domain applied against weapon systems, radar systems and wireless communications and “involves the use of EM energy, direct energy or anti-radiation weapons to attack personnel, structures or equipment with the intent to degrade, neutralize or destroy enemy combat capabilities “.
The Electronic Attack, depending on the mission carried out, can be divided into: Offensive and Defensive.
It can be performed with active (radiating) or passive (non-radiating or re-radiating) means.Electronic protection (EP): is the branch of the Electronic Warfare (EW) domain with the task of reducing or eliminating the effects of the enemy’s electronic attack on friendly sensors such as radar and radio.
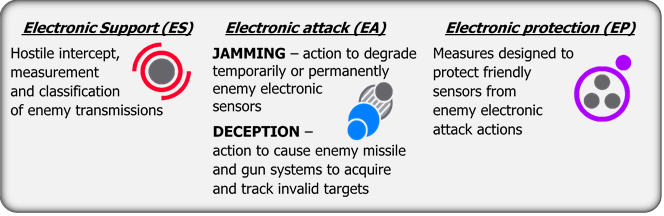
Figure 1: Electronic warfare major subfields
Historically it must be remembered that a previous subdivision of the EW included Electronic Support Measures (ESM), Electronic Counter Measures (ECM), and Electronic Counter Counter Measures (ECCM).
Electronic Warfare (EW), beyond its historical role of passive intelligence and protection and active attack, has evolved for several years becoming an essential element in the deployment of systems of systems in the field of EMSO (Electro-Magnetic Spectrum Operation).
Today, more than in the past, for this reason EW is not limited to the equipment that performs it but is a high-level function of the platform and in the case of a System System it is a high-level function of the System of the System itself.
The EW Functions are distributed across the entire platform and also among platforms with modular and scalable architecture and must be integrated to set up EW cooperation both in platform and multi-platform through:
- An EW network layer that integrates EW functions at platform level (System EW layer).
-
An EW network layer that integrates EW functions across platforms to enable the System of Systems EW network to operate.
As all components of military operations are spectrum-dependent and networked systems, the EW mission has evolved to control, manage and secure our use of the electromagnetic spectrum (EMS) in order to maintain essential network and data link services through secure segments of the EMS to transport, share, archive, protect and disseminate critical information.
On the other hand, the adversary use of the EMS must be known, controlled and denied in order to block and/or confuse the correct flow of information to delay or prevent the adversary decision-making process.
In short, the new mission requirement will be passive and active protection/attack of the “Network”: our unchallenged use of EMS is the ENTITY to be protected and secured, and the enemy’s use of EMS is the ENTITY to be hindered, neutralized and even destroyed.
This evolution is pushing in the direction of SOFT weapons, with an overflowing contribution of digital and SW technologies.
We can use the “cold war” acronym NBC (Nuclear, Bacteriologic, and Chemical) and transform it in NUC (Net-centric, Unmanned, and Cyber) to define this epochal change.
According to the consolidated doctrine EW is any action involving the use of the Electro Magnetic Spectrum (EMS) or directed energy to control the spectrum, attack of an enemy, or impede enemy assaults via the spectrum.
The purpose of electronic warfare is to deny the opponent the advantage of, and ensure friendly unimpeded access to, the EMS.
EW can be applied from air, sea, land, and space by manned and unmanned systems, and can target humans, communications, radar, or other assets.
EW is described as having three major subfields (Figure 1): Electronic Support (ES), Electronic Attack (EA) and Electronic Protection (EP), but according to the evolution of the reference scenario and, consequently, of its terms of use and to underline that EW is part of EMSO (Electro Magnetic Spectrum Operations), the word “electronic” is recently replaced by “electromagnetic” generating the new acronyms EMS, EMA, EMP.
Cyber warfare involves the use and targeting of computers and networks in warfare to gain a military advantage by gathering significant information from an enemy or interfering with the enemy’s ability to move information over the Internet or other networks or to process information within a computer. Cyber also impacts the normal operation of infrastructure, institutions, Command and Control, Communications, and Computers.
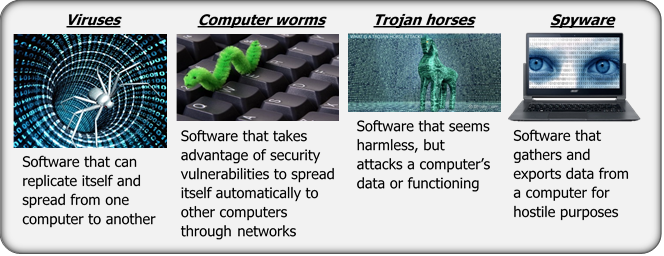
Figure 2: Cyber EW payloads
The question is:
“Should electronic warfare techniques like deception and jamming be grouped together with seemingly related skills like cybersecurity and signals intelligence, or should they be treated as different disciplines?”
The answer is towards convergence by including all the different technologies in a single integrated architecture that is supported by a powerful real-time management software.
In pursuing this vision, systems must become more spectrally efficient, flexible, and adaptable, and spectrum operations must become near real-time and able to integrate spectrum management, network operations, EW, cyberspace, and intelligence.
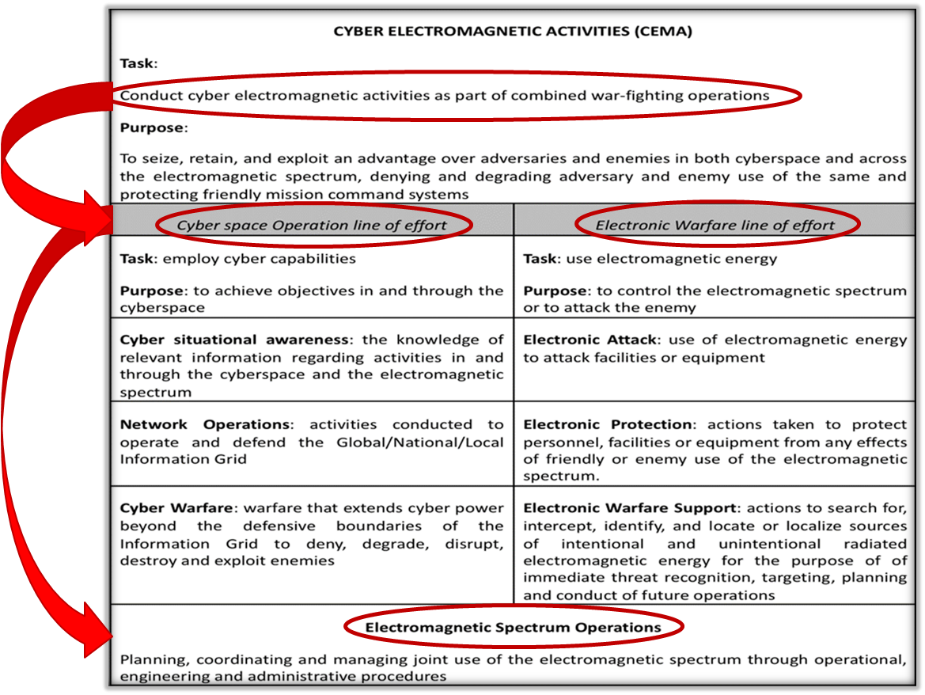
Figure 3: CEMA Task definition
The new target of EW will be to gain the Information Dominance that is the operational advantage established from fully integrated information capabilities, systems and resources to optimize decision-making and maximize war-fighting effects in the complex battlefield environment of the 21st Century.
Future systems will not only be able to use RF transmitters to jam enemy radar and communications, but also to insert viruses and other destructive computer code into enemy systems to spoof or disable them.
This extension of EW definition is a real Spectrum Warfare that starts from traditional EW, but adds cyber warfare optical warfare, navigation warfare and includes also the tactical use of signal intelligence.
This new scenario creates a new discipline, CEMA (Cyber Electro-Magnetic Activities) that can be defined as “The synchronization and coordination of cyber and electromagnetic activities, delivering operational advantage thereby enabling freedom of movement, and effects, while simultaneously, denying and degrading adversaries’ use of the electromagnetic environment and cyberspace”*.
*CEMA Capability Integration Group (CIG)
This new concept introduces a new order of battle oriented at disrupting or degrading enemy functionalities in military operations which are more and more net-centric and computer-centric.
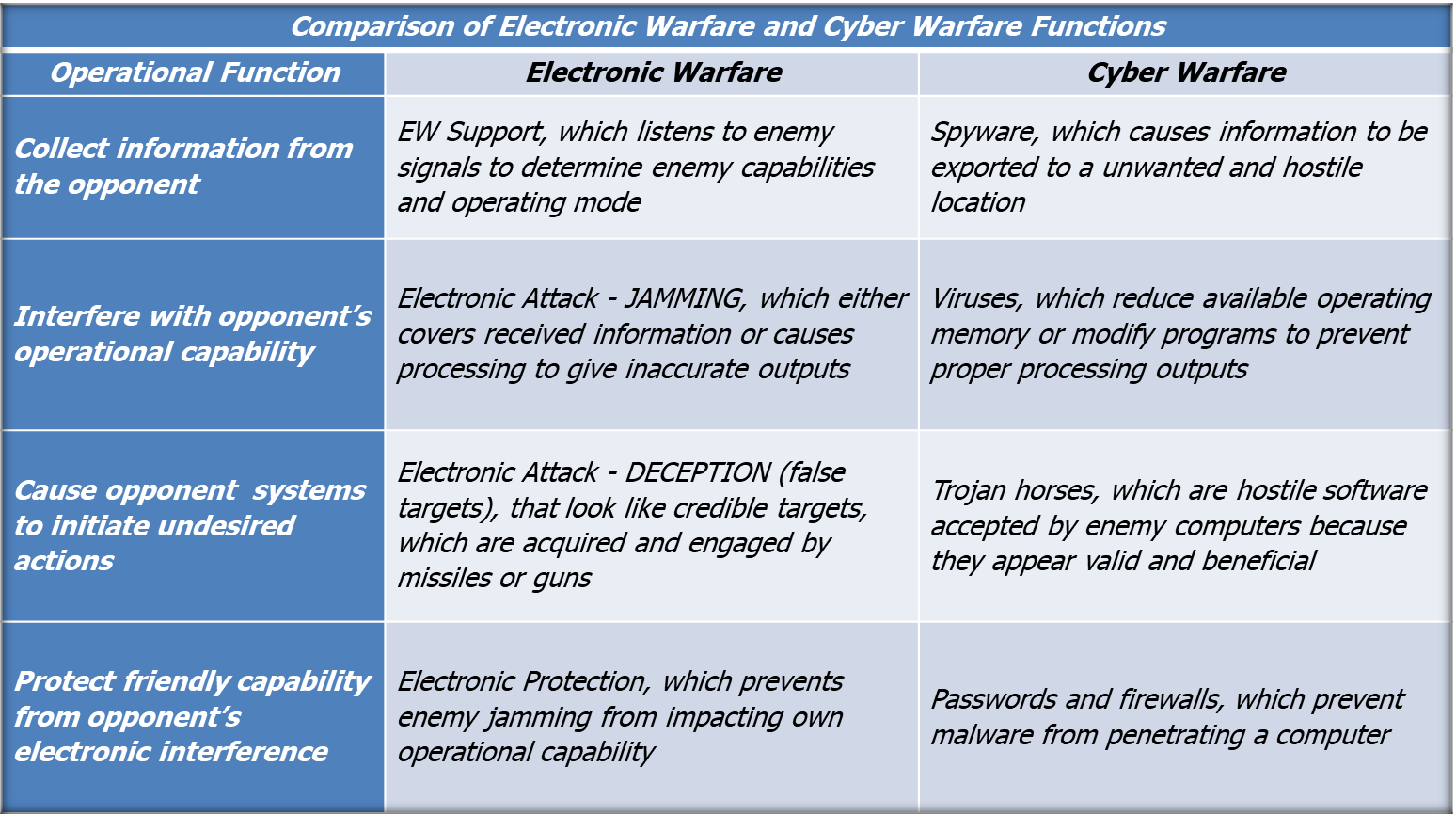
Figure 4: Similarities between Electronic Warfare and Cyber warfare
In this new scenario, a convergence between EW and CW (aka CEMA) is one of the next pillars to create a new parallel for common ops.
CEMA deliver effects that deny or degrade spectrum allowing for the control and exploitation of the network.
In the future and in response to the new role of EW as the discipline that allows the control of Spectrum based operations, several different capabilities must be implemented and integrated:
-
Net-centric EW that differs from conventional NCW because it needs wide band, near real time communications.
In a nutshell, blue force platforms will not only collect SIGINT to enhance self-protection but will share this across the force and jamming will not be performed by a platform alone but with the synchronized cooperation of several platforms (cooperative jamming) using Line-of-Sight (LOS) and Beyond LOS (BLOS) dedicated communications links. -
Collaborative EW that is the new frontier of Electromagnetic Spectrum Operations (EMSO) and is not limited to EW but influences also SIGINT and Spectrum Management in general.
EW evolves in “Collaborative EW” based on net-centric architecture needed to ensure the coordination of assets, expertise, knowledge and tools in order to integrate EW systems in the platform and across the cooperating platforms.
Collaborative operations suggest the definition of an EW layer in which the Information Management Organization collapses into a Command & Control Information structure.
Collaborative EW firstly encompasses Common Engagement Capability, as the availability of a sensor network, distributed in all domains of warfare (air-sea-land-space-cyber), plus tools and infrastructures combining data from multiple search sensors into a single, real-time, composite track picture. -
Cognitive EW that is the capability to interface and master the spectrum with devices that intelligently find and exploit spectrum and network vulnerabilities to create highly specific effects, including cyber effects.
The idea is bio-inspired or better, human-inspired and seeks to emulate a cognitive and autonomous approach to the environment in terms of observing, orienting, deciding, acting and applying experience.
Cognitive EW defines a System that learns from experience and is heavily based on Artificial Intelligence and Machine Learning concepts.
In this field of application particular emphasis is given to Cognitive Jamming that is a leap forward in the context of Electronic Warfare.
Jamming passes through different steps of processing from threat detection to jamming execution, a Cognitive approach is applicable to all the steps of the process.
For instance, “Threat Detection”, “Threat Identification” and “Jamming Program Selection” traditionally rely on imperative algorithms based on some form of explicitly defined waveform taxonomy that is supposedly able to represent threats and on a carefully built “Jamming Library” which contains a collection of Jamming Programs tailored for being effective against well-known (Identified) threats.
Applying the cognitive mind-set to these blocks can lead to:-
Removing taxonomy constraints using a machine learning-based paradigm to perform detection and identification processes.
-
Synthesizing in real time the most appropriate Jamming Program (JP) against a given threat
-
The solution is far from being easy in fact this new approach implies some degree of “smartness” that must be brought into the System and that depends on some key technology and methodology.
Future requirements for all Spectrum Dependent Systems, from radars to radios, from satellite services to global communications, from telecoms to EW, will be:
-
Efficiency: the minimum possible occupation of spectrum resources is essential taking into account the presence of other actors who make simultaneous use of the spectrum in the electromagnetic environment.
-
Flexibility and Adaptability: the access to the spectrum must be flexible and adaptable (for instance capability to operate in multiple frequency bandwidths) to allow access to the spectrum to other cooperating systems and increasing electromagnetic compatibility (EMC).
-
Agility: agility in spectrum operations, enhanced by the extensive use of artificial intelligence and machine learning, will enable the use of efficiency, flexibility and adaptability.
Traditional access to the spectrum, based on rules and constrained by technology limitations, are destined to fail and hence a new paradigm is necessary.
New areas of EW and Cyber are exploring Space Resiliency operations, methods, protection, and warfare are exploring challenges in this new frontier.







