Electro Magnetic Spectrum Operation (EMSO)
Since the Cold War, the potential for the EMS to support conventional military forces has been clearly understood by both Western and Eastern countries alike.
Hence, both parties have invested in Spectrum Dependent Systems (radars, radios, EW and SIGINT systems and systems of systems) for military and national security purposes.
The EMS has always been militarized, but the dual use nature of the EMS, the enormous dependency that the global economy has developed on EMS-based services and the impacts of technology miniaturization are combining to create challenges for all nations because of their reliance on services tied to the EMS.
Furthermore, adversaries are aggressively fielding electronic attack and cyber technologies that erode the ability to use the spectrum for joint operations, while the global wireless broadband industry is seeking to reallocate spectrum from defence use to commercial uses, to meet consumer demands for greater mobility and data connectivity.
We need to think of the EMS as virtual international critical infrastructure and all nations need to do what they can to protect and preserve the EMS environment.
Electromagnetic Spectrum Operations (EMSO) discipline
Modern military forces are required to operate in an increasingly complex Electromagnetic Environment (EME), which has recently been recognized as an “operational environment” by NATO, as referenced in MC 64/11 “NATO recognizes the Electromagnetic Environment as an operating environment.”
NATO doctrine recognizes that NATO operations are complicated by an increasingly congested and contested EME.
All modern forces conduct operations that depend on the use of the EME.
The recognized need for military forces to have access to and utilize the EME creates vulnerabilities and opportunities for EM spectrum warriors.
Therefore, a new operational discipline has been set up accordingly, named Electromagnetic Spectrum Operations or EMSO.
EMSO (see Figure 1) consist not only of “traditional” Electronic Warfare (EW), but includes several other disciplines which operate in the Electromagnetic Environment, such as Signals Intelligence (SIGINT) as part of Information Operations, Spectrum Management and Cyber Electromagnetic Activities (CEMA).
-
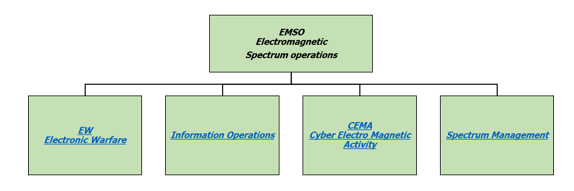
Figure 1: EMSO and related branches
Electronic Warfare (EW) remains the main combat discipline of EMSO.
It is referred to as any military action involving the use of electromagnetic or directed energy to control the electromagnetic spectrum, to deny the use of the spectrum to the opponent in a preventive manoeuver, to counteract the spectrum-based actions in a reactive/defensive way or to attack the enemy using the electromagnetic spectrum.
The ultimate purpose of EW is to deny the opponent the advantage of the EMS, and ensure friendly unimpeded access to the Electromagnetic Environment.
EW can be applied from air, sea, land, and space by manned or unmanned systems, and can target humans, communications, radar, or other assets generally identified as Spectrum Dependent Systems.
For those who are not familiar with the topic, EW is generally described as having three major subfields:
-
Electronic Support (ES), which involves hostile intercept of opponent transmissions.
-
Electronic attack (EA), in which enemy electronic sensors (radar and communication receivers) are degraded temporarily or permanently by the transmission of noise-like signals (JAMMING), or credible false signals that cause enemy systems to acquire and track invalid targets (DECEPTION).
-
Electronic Protection (EP), which is a set of measures designed to protect friendly sensors from enemy electronic attack actions.
In other words, Electronic Warfare aims at the Spectrum Dominance in a combat environment.
In recent years, Electronic Warfare has included Navigation Warfare (NAVWAR) too. The critical dependence on Position-Navigation-Timing (PNT) information and services of humans, businesses, war-fighters or any kind of platform in all domains has generated a specific discipline.
The detection, denial, deception of all PNT signals and infrastructure, from radar altimeters to satellite-based time and position reference systems represents a new challenge for EW warriors.
Similarly, the availability of trusted and robust PNT information is a key factor for any military, military-supported and homeland security operations in peacetime, crisis and wartime.
Therefore, protection of PNT information from both electromagnetic and cyber-attacks represents an engineering challenge in terms of both countermeasures and resilience.
Signals Intelligence is included in the wider framework of Information Operations and refers to the ability to exploit signals, data and information that rely on the use of the Electromagnetic Spectrum as a physical layer.
Since the beginning of human history, Information is a combat resource.
In the last few decades, defence and security environments have been characterized by their high rate of change, both from a threat perspective as well as from the preventive or defensive tools and doctrine perspective.
In this more and more diversified, unpredictable, , digital and interconnected world, devices and functions for Information Management are vital for sovereignty.
In military, military-supported and homeland security operations, mission success is strictly dependent on the correct flow of information as well as the capability to correlate and fuse information from different sources and with existing knowledge, in support of rapid decision making.
Robust, protected, resilient and reliable information infrastructure (both physical and logical) is needed to:
-
support the overall information environment
-
allow uninterrupted communication between deployed units and forces ashore.
Information content will serve as the basis from which nearly all decisions will be made, enabling armed forces to more effectively manoeuvre and coordinate actions that target and engage opponent forces.
Therefore, information infrastructure must be able to maintain essential network and datalink services across secured wired and wireless segments in order to transport, share, store, protect and disseminate critical information.
Modern systems (civilian, national infrastructure, military) are today more and more interconnected via communication networks without fixed infrastructure, entering the categorization of Spectrum Dependent Systems.
On the other hand, they are more and more based on the use of computing capability to elaborate data and information, manage their functionalities, and control their status.
A computing system is a system whose performed functionalities are mainly implemented and/or are enabled by means of programmable devices, which include: DSP (Digital Signal Processing), FPGA (Field Programmable Gate Array), CPU (Central Processing Unit), GPU (Graphic Processing Unit) and moreover, in terms of physical components, memory devices, interfaces, operating systems and application logics.
Personal Computers in their various forms are icons of the contemporary Information Age and are what most people think of as a computing system or computers.
However, the embedded computers found in many devices from MP3 players to radars on fighter aircraft and from toys to industrial robots are the most numerous.
Therefore, a computing system which makes use of a wireless interface, creates a vulnerability that can be exploited in order to:
-
collect sensitive information, which can be used for any operation within the network,
-
force access to the network, to take advantage of the services of the network itself,
-
degrade the performance of the network, to include denying use of the whole service,
-
degrade/modify the performance of one or more node of the network, by introducing dedicated data stream and inserting/activating malicious code in the computing system.
For example, a hypothetical device operating against a cell phone network, for instance, may not just blindly inject energy into the cell phone band, as a traditional jammer does.
Instead, it might selectively jam certain frames destined for particular handsets, causing a directed EW effect at the physical link.
It might also inject additional data into the link, causing cyber effects at the protocol or user level.
For instance, forwarding tables could be updated in a way that partitions some users from the network or additional data could be inserted into a user session, invalidating the information the user gains from the session.
For a number of years, military operations have used electro-magnetic attacks to disrupt enemy radars on the battlefield, but today the access and manipulation of the EMS and/or the data and information carried by EMS lets us foresee many additional capabilities.
In other words, the Electromagnetic Spectrum is an entryway for cyber actors.
Electronic Warfare and Cyber Warfare (CW) are trying to accomplish similar tasks against the opponent:
-
Collect information from the opponent
-
Interfere with the opponent’s operational capability in accessing/using its resources
-
Cause the opponent systems to initiate undesired actions
-
Protect friendly capability from the opponent’s electronic interference
They can be used in conjunction with each other and thus may be viewed as two sides of the same coin, which is often described as Cyber EW or Cyber Electromagnetic Activity (CEMA).
Finally, Spectrum Management refers to those interrelated functions of frequency management, host nation coordination and joint spectrum interference resolution that together enable the planning, management and execution of operations within the electromagnetic operational environment during all phases of military operations.
Command and Control over Electromagnetic Spectrum Operations
Given the increasing complexity of the operational environment, it is clear that EMSO demands a level of coordination and synchronization, which is impossible without specialized capabilities to support situational awareness, coordination and prioritization of actions across the Electromagnetic Environment. Therefore, Command and Control of EMSO is growing as an emerging need, including the development and implementation activities associated with the supporting functional services (Mission simulation, Mission support and Training).
EW and SIGINT assets in their fundamental role of passive intelligence and active protection, have evolved in the last several years becoming important elements of C4ISTAR systems and their system of systems.
-
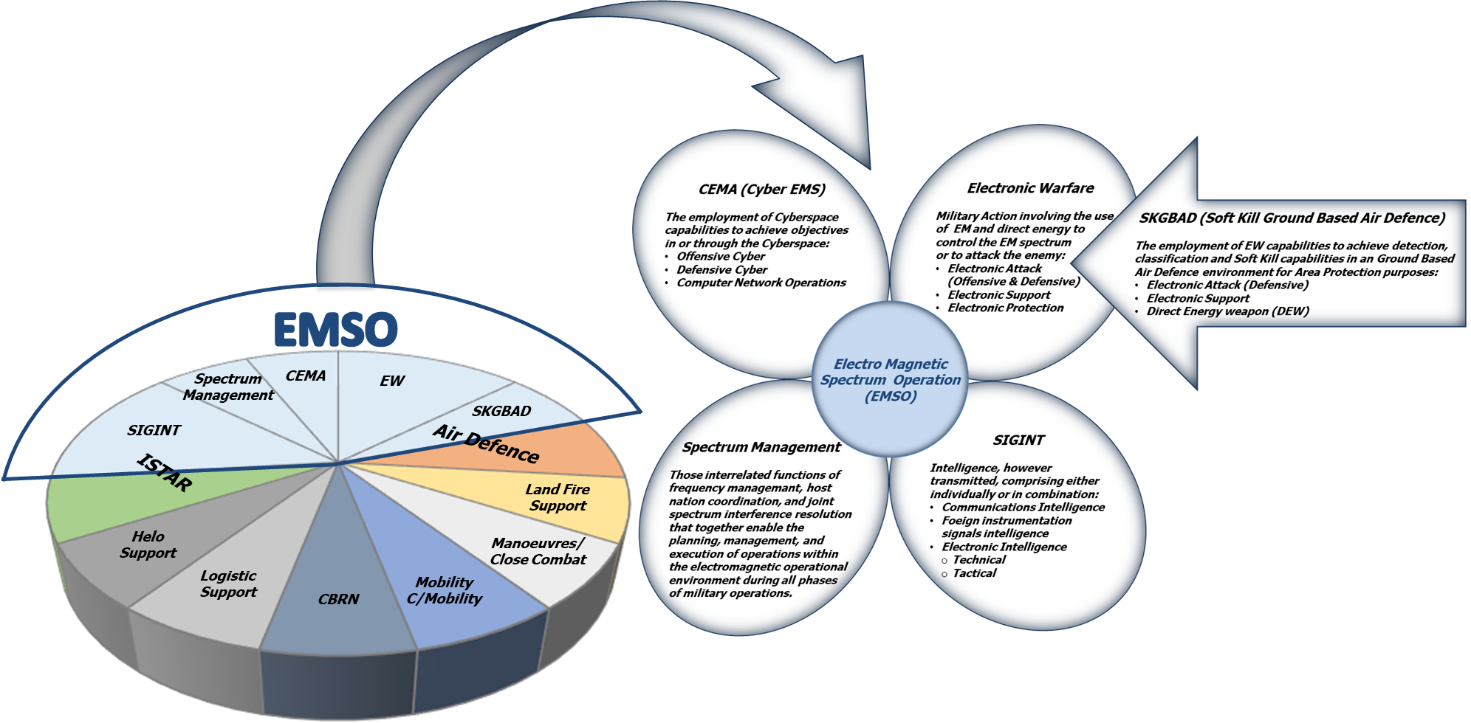
Figure 2: EMSO as part of C4ISTAR
EWC4 (Electronic Warfare Command, Control, Communications, Computers), inside the larger C4ISTAR (Command, Control, Communications, Computers, Intelligence, Surveillance, Target Acquisition, Reconnaissance), supports integration, coordination, planning, execution, assessment, validation and de-briefing of the operational functions:
As supporting functions, it includes:
-
EMSO War-Gaming/Mission support
In the future and in response to the new role of EW and SIGINT assets, net-centric based operations (Net-centric EW) will assure the coordination of assets, expertise, knowledge and tools in order to integrate EW systems installed on board the same platform and on board different platforms in order to create a SYSTEM OF SYSTEMS.
Military Operations in a spectrum degraded environment
The Electromagnetic Spectrum is a congested, contested, competitive and continuously changing domain of operations.
In modern and future operations, spectrum degradation must be considered the norm rather than the exception, ranging from degraded communications, interrupted PNT services and even cyber-attacks.
A general need for spectrum access where and when needed will increasingly be essential for mission success.
Future requirements for all Spectrum Dependent Systems, from radars to radios, from satellite services to global communications, from telecoms to EW, will be:
-
Efficiency: the use of the minimum amount of Electromagnetic Spectrum resources necessary to ensure maximum operational effectiveness in fully accomplishing the required mission while taking all practicable steps to minimize impacts to other systems in the Electromagnetic environment:
-
Flexibility and Adaptability: the capability of a spectrum-dependent system to exploit various opportunities to access the spectrum – e.g., multi-band operation, increasing the ability to share spectrum with other systems (domestic or foreign, federal, or non-federal), becoming more tolerant of interference;
-
Agility: agile spectrum operations will enable spectrum-dependent systems to utilize their flexibility and adaptability to achieve mission success in rapidly changing Electromagnetic environments.
Traditional access to the spectrum, based on rules and constrained by technology limitations, are destined to fail and hence a new paradigm is necessary.







