Counter Drone
The detection, identification, neutralization and (when possible or allowed) destruction of such UAS, used as unconventional threats when flying near key infrastructure or sensitive areas (e.g. government buildings, high-profile event locations, prisons, military compounds), has therefore become a critical capability. So far, traditional countermeasures have demonstrated their weakness in this regard. Unconventional threats require advanced solutions, and many industrial and government initiatives are rising to meet this new threat.
To neutralize such kind of threat and perform a soft kill action, jammer and deception (namely, Electronic Warfare or EW) are today the most feasible approach and many examples of in-service products exist, with several degrees of sophistication.
In the basket of non-destructive techniques, low power laser technologies and low power electromagnetic pulsed sources are emerging, to negate the threat the use of electro-optic sensors or the use of the electromagnetic spectrum.
Exploiting cyber capabilities is an important vector to counter the mini drone threat, though respective solutions are still immature and require superior knowledge, skills, and tools in the cyber domain.
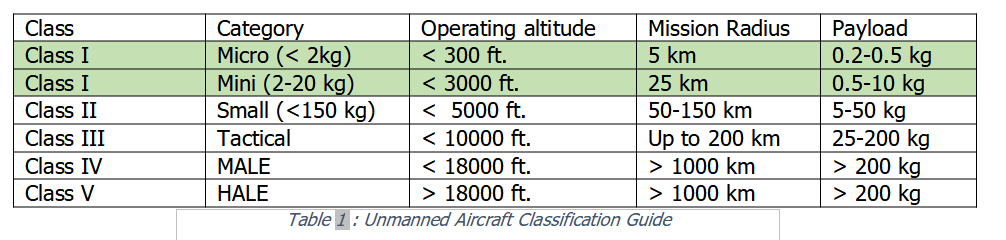
UAS can be classified, as summarized in Table 1, as a function of weight, altitude and payload (source: U.S. Army Roadmap for UAV 2010-2035).
Categories first focus on classes of weight, that are further divided based on the operational altitude.
CLASS I, which is the subject of this discussion, refers to platforms up to 20 kg.
Defending against small drone threats is a complex issue, since it is not only about eliminating the drone to prevent it from completing its mission. Successful defence must ensure the immediate detection, classification and identification of the object prior to neutralizing it in a secure framework for the safety of the people on the scene as well as minimizing collateral damage.
Given the physical and kinematic characteristics of the drone and the typical modes of use, a multiple sensor approach is necessary to improve the detection capability.
Sensors that can be integrated in Counter Drone Air Defence System are:
- • Radar
- Detection, tracking and range estimation of aerial targets are the main tasks performed by the radar. However, mini drones are hard to detect and identify due to very low radar signatures and related difficulties to exploit the Doppler Effect.
- Active radar is the prior sensor due to its unique capability to estimate the distance of the threat and consequently its time-of-arrival.
- Estimated time-of-arrival is the key element in the decision making process of the reaction chain.
-
- The main characteristics that are currently driving the choice (and will drive much more in the future) are:
-
- ◦ Native 3D radar (azimuth, elevation, range), based on electronically scanning antenna, able to generate one or multiple beams in azimuth and elevation.
-
- This is justified by the operational requirements to cue efficiently the camera, to have a sudden confirmation of the nature of the threat, and to steer the shooters (soft/hard) in both azimuth and elevation.
-
- ◦ Simultaneous tracking of multiple threats to counter attacks of coordinated drones or cooperating swarms.
-
- ◦ AESA architecture that ensures the faster reaction time to alarm and activation of the countermeasure chain and high reliability.
-
-
- ◦ Designed for easy transportation and rapid deployment, even by a single soldier, which requires the radar to be “tactical” by design.
-
- • Camera
- Together with electromagnetic sensors, thermal cameras are essential devices, usable under low visibility conditions and at night.
-
- The main issue is that the range of threat acquisition is less than the radar detection range.
-
- This requires the camera to be cued (in both azimuth and elevation) by the radar track and requires the radar to continuously track the target.
-
-
- Usually cameras are human-operated and identification confirmation is human-assisted.
-
- • EM sensor
-
- Electronic Defence systems are commonly integrated in the most effective counter-drone solutions.
-
- These devices quickly detect the presence of radio signals used to send the commands from the pilot to the drone (uplink) and to send data and images from the drone to the command post (downlink).
-
- For commercial drones, those radio signals are transmitted on well-known and standardized frequencies, relatively easy to be intercepted with electronic surveillance in automatic mode, even though complex wave modulations are often superimposed to the carrier signal.
-
- Passive interceptor of this type have the capability to automatically analyse the radio wave and allow the identification of the threat based on the transmitted waveform (Non Cooperative Target Recognition).
-
- This is a very interesting complement to the radar detection and could be used also for false alarm reduction and target discrimination from birds or even friend drones.
-
- Furthermore, passive geo-location techniques can be put in place to locate both the drone and the control station.
-
• Acoustic
During flight, drones generate noise both in the audible frequencies and in the ultrasounds. Acoustic sensors reveal the presence of mini drones as well as helping to classify the target based on noise characteristics specific of the drone model.
However, the operational range of acoustic sensors is limited to a few hundred meters. At higher distances, drones are lost in background noise. On the other hand, radars have a blind spot at shorter distances. This means the acoustic sensor, made up of an array of microphones, is the ideal gap filler for radar systems to cover both long and short ranges. Being relatively cheap, acoustic sensors are efficient tools for the continuous surveillance of particularly sensitive areas.
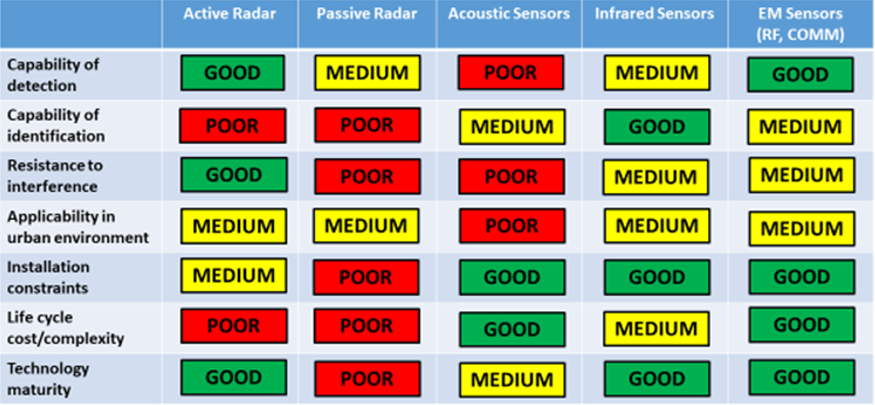
Figure 1: Counter-drone eligible sensors – “What is best” analysis
Every sensor technology has pros and cons, touching a variety of factors: operational performance, installation constraints, life-cycle costs, modularity and scalability, military or non-military use, maturity.
Figure 1 shows a qualitative comparison among the eligible sensor technologies.
The conclusion is that there is no “silver bullet” to detect-classify-discriminate-identify the threat and that a plethora of sensors, correctly functionally integrated, is needed to enhance the probability of detection and the correct trigger of the reaction chain.
Human-in-the-loop is also a key factor at least for today policies and tactics, and the complexity of the technologies put in place together with the unpredictability of the threat require a high level of skill.
Detection and identification are essential, but they are only the preliminary steps in solving the problem of removing the rogue drone from the scene and/or its neutralization.
“Hard Kill” or physical destruction options are limited to combat zones or an open field, where the consequences of falling wreckage, ordnance, or other harmful items are generally irrelevant.
In an urban scenario, a different approach aiming at a “Soft Kill” philosophy is preferable. The following described options have currently been proven as feasible and effective.
Effectors that can be integrated in Counter Drone Air Defence System are:
- Jamming
A first option is to affect previously detected and identified radio signals, which would subtract and sever the control of the drone from the operator.
Then it could be forced to land in a safe area or to crash without risking collateral damage.
The simplest technique is to generate jamming signals against the control link, delivering enough power to negate the use of the electromagnetic spectrum.
According to the programmed modes, the drone then automatically enters into fail-safe mode causing it to land or return home.
This “brute force” approach however requires generating a huge amount of electromagnetic power and broad spectrum jamming of the whole area, which may also result in the undesired suppression of friendly communications.
A more sophisticated and selective technique is so-called “Smart Jamming”, which consists of jamming the control signal only in some specific timeslots, according to the specific protocol used by the radio remote control.
Smart Jamming techniques require the a-priori knowledge of the waveform and its coding that means a library of control signals protocols.
This is obtained by a huge a-priori activity of reverse engineering and intelligence that gives additional strength to the blue forces in countering the threat. - GPS Deception/Spoofing
One should argue that this technique only applies to UAV large enough to be utilizing GPS.
Many mini and micro UAV will likely be too small and short-range to have GPS.
But size may not really be limiting the use of GPS.
Indeed modern smart phones exploit lots of inbuilt functions and features taking advantage from the positioning and timing information.
Miniaturization of GPS receiver and global availability of positioning systems today are integrated in many UAV available on the open market (5-10 k€, not really toys…).
The most effective albeit complex technique is Global Positioning System (GPS) spoofing, provided the targeted UAS is using satellite navigation.
The technique consists of seducing the UAV’s GPS receiver to recalculate its position and then deviating its path in accordance with pre-planned countermeasures.
To this end, a spoofing device transmits imitated satellite signals while deceiving the target with formally correct but false position data.
This requires knowing the exact position and speed of the drone, which can be provided by the radar sensor.
Precise scheduling of each spoofing phase is needed to reduce the effectiveness of counter-countermeasures of certain smart, GPS-based guidance systems. - Direct Energy Weapons
In addition to these soft-kill techniques, weapons are being developed that produce a high-power microwave electromagnetic pulse that is highly effective against electronic equipment.
With a specifically shaped antenna, or emitter, the energy can be focused to produce effects within a confined area and limited range.
Under certain circumstances, such weapons could ideally complement the other techniques to neutralize small drones.
Under this category, it should be mentioned also the use of high power laser.
The technology, even if still not fully mature, is demonstrated to be highly effective, generating the destruction of the target.
The major issue is linked to the safety of the humans operating the laser gun. - Blue drone
The blocking of the enemy drone, i.e. the neutralization of the threat, can also take place physically thanks to the use of friendly drones (blue force drones blue drones) also known as drone hunters.
The family of drone hunters is young but is populating very rapidly, inside the family we can list:
◦ Drone catcher: is a kind of drone (often a multi-copter) equipped with a net fired by a gun.
After detection, the drone catcher is rapidly deployed to intercept the moving target, under control of a remote operator.
As soon as it gets close to the victim drone, using multi-spectral on-board sensors, it locks the net gun onto the target then safely captures it by firing the net, tows it away to a safe location and releases it there.
◦ Collision Drone: this is a drone normally remote operated.
After detection, the drone is rapidly deployed to intercept its prey, locks on it, and disables it by collision.
◦ Weaponized Drone: is a kind of drone equipped with explosives.
After detection, it is rapidly deployed to intercept the moving target, under control of a remote operator. As soon as it gets close to the victim drone, it fires the explosives to damage the target. This application is particularly useful to counter drone swarm attacks (one-to-many).
All the above-mentioned solutions can be upgraded to a higher automation level making wide use of on-board AI and advanced machine vision processing making them patrolling a given airspace.
Within the assigned area, they can autonomously detect, intercept and neutralize any unwanted objects.
The new generation hunter drones can operate as standalone units or be integrated inside a higher-level counter drone infrastructure.
From the operational point of view, a counter-drone system should be able to:
- detect, classify, track, identify and counter UASs (single and/or multi-UAVs) in defence scenarios using multiple technologies;
- operate from detection to counter UASs also in civil scenarios;
- deliver and update real-time operational picture and alerts;
- integrate into multilayer C2 system with cross-security-domain approach.
Two main operational modes must be available:
- Soft
- Hard (integrating Soft Kill capabilities and supporting functions):
– provide a range of selective mitigation alternatives with the ability to evaluate mission success probabilities and resulting drawback;
– require limited logistic support for deployment and maintenance;
– require minimum operator effort for decision making;
– provide dynamic scalability of sensors and effectors;
– facilitate the incorporation of counter UASs in security and defence systems for fixed and deployed asset;
– be able to operate in a wide range of climate (e.g. arctic, subtropical) and weather (e.g. rain, fog, snow) conditions.
Therefore, a counter drone solution (example is given in Figure 2) is not just the sum of sensors and shooters, it is a comprehensive and continuously evolving Multi-Domain Area Protection Capability aimed to DETECT, DISCRIMINATE, IDENTIFY and NEUTRALIZE DRONE threats.
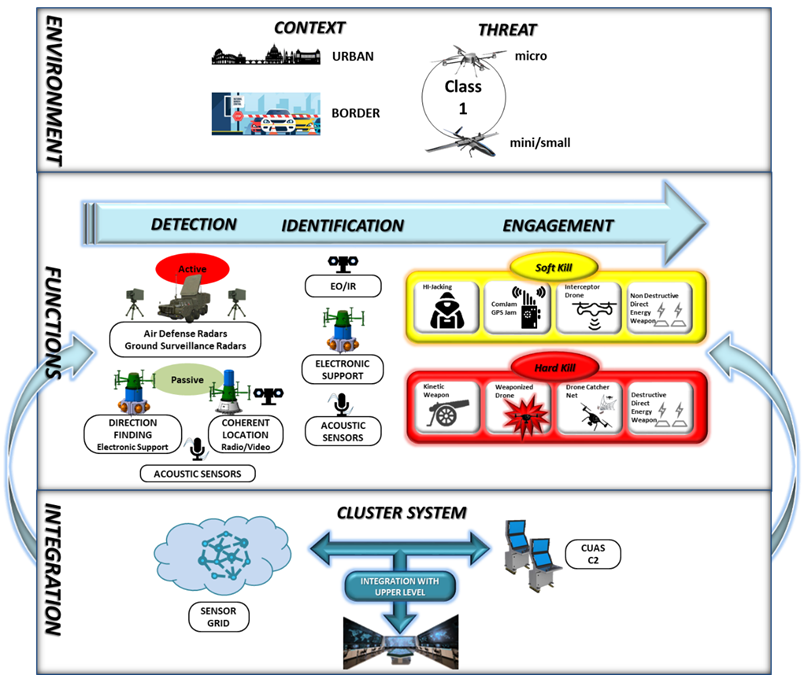
Figure 2: C-Drone possible solution
In any case, every Counter-Drone solution, even if modular and scalable according to the operational scenarios and the needs of the final user, will be several times more complex than the threat, requiring a plethora of assets deployed. Furthermore, the control of these assets will require highly qualified and best-trained operators, whose mission preparation needs to be much more professional and complex compared to the relative simplicity of the threat.
The costs of the defence could therefore be magnitudes higher than the cost of the attack. This is asymmetric warfare.








