Communication Electronic Attack
Armed Forces use communication links to move signals through the Electro-Magnetic Spectrum (EMSO) to where they are needed in a dynamic engagement scenario.
Also the communications to and from remote upper level command & control posts and to and from other combat platforms are made through EMS and/or satellite communication links.
This creates wireless communication networks based on electromagnetic interconnectivity that are vital for the tactical effectiveness and survivability of every element of the system of systems.
Wireless or wireless/wired networked systems, both military and civil require the access to the EMS to operate effectively.
Communication jammers applied against Wireless Sensor Communication Networks, interfering with the radio frequencies used by sensor nodes in order to impede or confuse enemies’ communications to stop or delay their decision chain.
In terms of operating platforms, the CECM exploits its Electronic attack capability either in Stand-Off platforms or in Stand-In platforms, respectively with the specific deployed jammer.
The comm-jamming signal is an intentional radio signal that disrupts communications:
- For analogue communications, it decreases the analogue communications signal-to-noise ratio generating a quite high Jammer to Signal ratio (JSR) in order to desensitize the radio’s receiver.
- For digital communications, it affects the victim receiver increasing its BER (BIT Error Rate) over the threshold for correct information reconstruction or impairing the receiver’s clock recovery and bearer synchronization circuits, rendering the victim receiver inoperable by disrupting its internal information flow.
Cyber Electro Magnetic Activity (CEMA) revolution in Communication Electronic Attack
Electronic Warfare enters electromagnetically in the enemy system functionality.
Electronic Support systems receive transmitted signals from hostile transmitting antennas and hence malware Electronic Attack enters enemy receivers through the enemy receiving antennas.
Cyber Warfare requires that the malware enter the system as software, that is to say, that the system is jammed from the Internet, a computer network, a floppy disk, or a flash drive.
It is true that modern weapon systems are more and more “software defined”, and, because of high mobility requirement, they need to exchange information through the EMS. Developments of digital data exchange technology have given the possibility of exchanging data between computers via wireless networks.
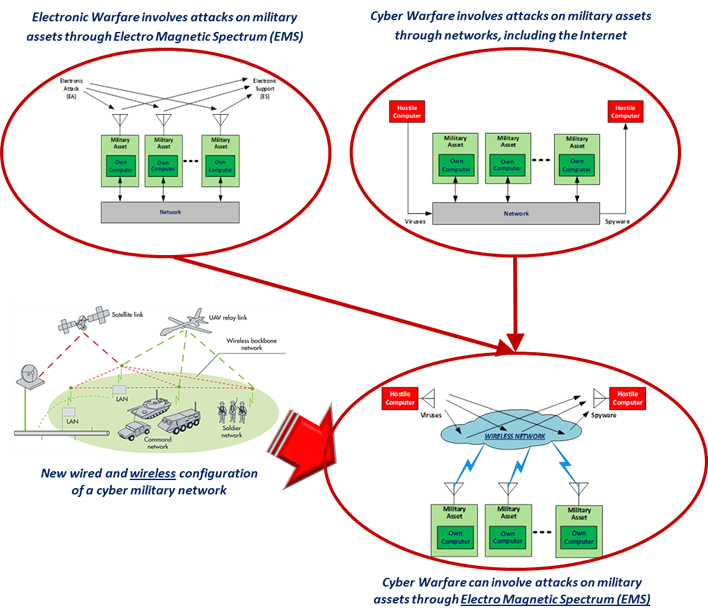
Figure 1: Convergence between EW and CW
This data exchange opens the door to merge Electronic Warfare with Cyber Warfare and to give to a communication jammer the capability to disturb computer networks with Cyber-attacks. New communication jammers must have also the capability to carry Cyber payloads to be delivered to the target computer through the EMS and through the wireless network.
Communication Electronic Attack includes the capability to perform Cyber Warfare: Electronic Warfare and Cyber Warfare work in conjunction and thus may be viewed as two sides of the same coin, which is often indicated as Cyber EW or Cyber Electro Magnetic Activity (CEMA).
Cyber payload (Figure 2) is injected in the target computer through the EMS and through the wireless network.Then the network is infected and the payload is activated inside the first networked computer (“n-click”) and then bounced back to the other servers and computers/computing systems via the wired and wireless networks.
The nodes of networked systems physically reside in one of the warfare domains (air, land, sea, space), but the ability to achieve the mission objectives cannot be separated from the ability to control and to have freedom of action in cyberspace that, in this sense, is transversal to all other domains.
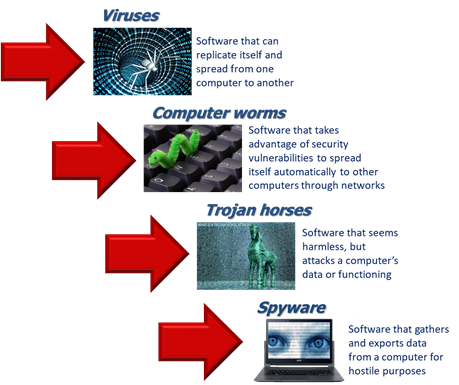
Figure 2: CEMA payloads







