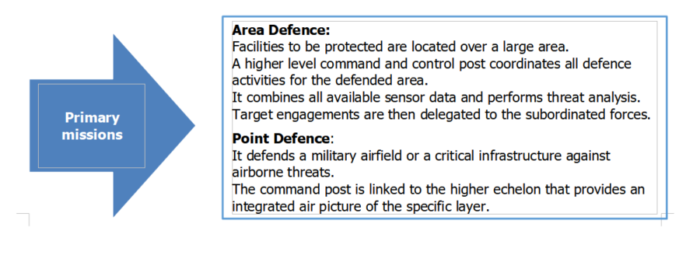
Area Protection Task
Modern Air Defence (AD) is an integrated and multi-layered structure to counter incoming threats with multi-spectral sensors/actuators delivering graded countermeasures at different intercept ranges.
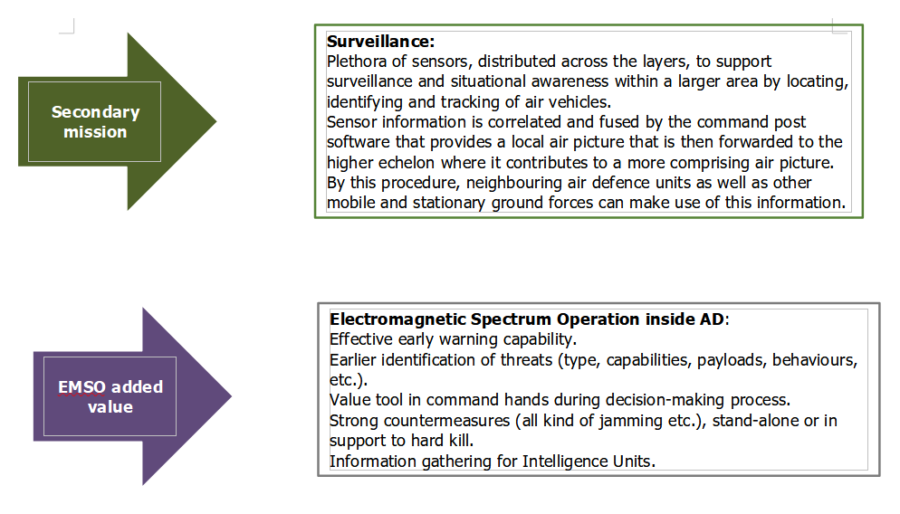
Modern forces are required to operate within an increasingly complex Electromagnetic Environment (EME), which has been recognized as an “operational environment” by NATO (ref. MC 64/11 “NATO recognizes the EME as an operating environment”).
A new operational discipline has been set up accordingly, named Electromagnetic Spectrum Operations (EMSO).
EMSO consists not only of “traditional” EW, but includes several other disciplines, which operate in the EME, such as Information Operation/SIGINT , Spectrum Management and Cyber Electromagnetic Activities (CEMA).
Nowadays, warfare environment calls for immediate reaction since information about the enemy’s position or about a surprise attack becomes available at short notice only and consequently:
- Air Surveillance should not rely exclusively on radars, but also on other means to get situational awareness without the drawback of being detected and possibly jammed by opponent assets.
- Defensive strategies should be developed, which are able to neutralize instead than destroy, thus reducing the danger of escalation
Air Defence is not only tasked with the kinetic suppression of the target, often its goal is to deny the accomplishment of the mission, especially in case of ISR missions.
For this reason, ESM/SIGINT capabilities can play an important role in both strategic and tactical surveillance of wide as well as of small critical areas.
Features such as:
- Non-Cooperative Target Recognition,
- Specific Emitter Identification/Fingerprinting,
- Covert Early Warning, which are typical characteristics offered by ESM/SIGINT systems, can really represent a gap filler/force multiplier in IADS.
Accordingly, ECM can be applied to any target, but especially to the tactical UAS target set, with the purpose of interfering with any RF receiver or jamming transmission. Systems susceptible to jamming actions are the avionics systems (e.g. altimeters), data and command links, SAR and D/GMTI radar, commercial mobile telephony, personal mobile radios (AM/FM), and global positioning systems (GPS).
The goal of ECM is to prevent the successful reception or transmission of data.
This may mean simple narrowband jamming (denying the platform the use of the jammed spectrum) or approaches that are more sophisticated. COMM ECM aims to exploit information contained within the data-link, which is more similar to a cyber-style attack. GPS ECM, consisting of jamming or spoofing, is simple due to the weakness of GPS signals.
However, GPS protection techniques are available to amplify the satellite signal and attenuate in the direction of the Jamming Signal.
Several options could be exploited:
- Negate or degrade the use of the electromagnetic spectrum to affect guidance or data transfer to the Ground Control Station (denial)
- Negate or degrade the use of the electromagnetic spectrum to affect the electromagnetic sensors on board the vehicle (deception)
- Make the UAS stream of the audio/video data not only to its Ground Control Station but also to the “hacker” station (hacking)
- Confuse the UAS with false GPS information, waylay it or direct in a wrong direction (spoofing)
The purpose of the Integrated Area protection System is to protect sensitive sites/critical infrastructures sparse over a large area.
This will be achieved by a system of systems net-centric architecture integrating different layers of protection: a lower operational layer composed of a number of U-SHORAD (ultra-short-range air defence) and V-SHORAD (very-short-range air defence) assets is federated within an upper operational layer (Common Command Post, C-POST) acting also as SHORAD (short-range air defence).
A central concentrated intelligence (powered by AI and ML CONCENTRATED INTELLIGENCE) resides in the upper operational layer acting as System C4.
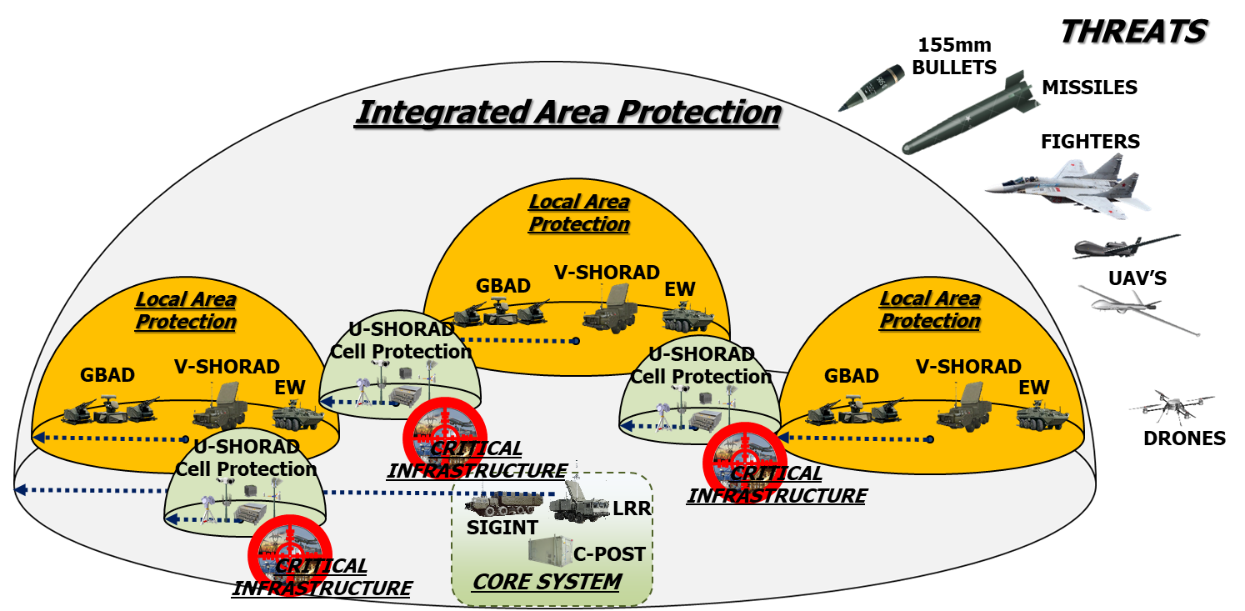
Figure 1: possible deployment of the assets/capabilities in the protected area
The assets in the lower operational level cooperate with each other under the control of the higher level and are equipped with AI and ML (DISTRIBUTED INTELLIGENCE) which act as subsystem C2. Each asset (whatever the level) is composed of a very varied panel of sensors and/or built-in or external effectors (soft kill and hard kill), correlated and associated through dedicated software, driven by an internal C2 software.
The networked and integrated architecture allows operating as a single system (each sensor of a local cell, in addition to managing the area entrusted to it, can act as an early alarm for the sensors of other cells, functioning as a pre-alarm and giving a real decrease in response time).
The Integrated Area protection System of Systems acts as a brick in the territory Air Defence and is perfectly integrated at operational level with other components of the IADS.
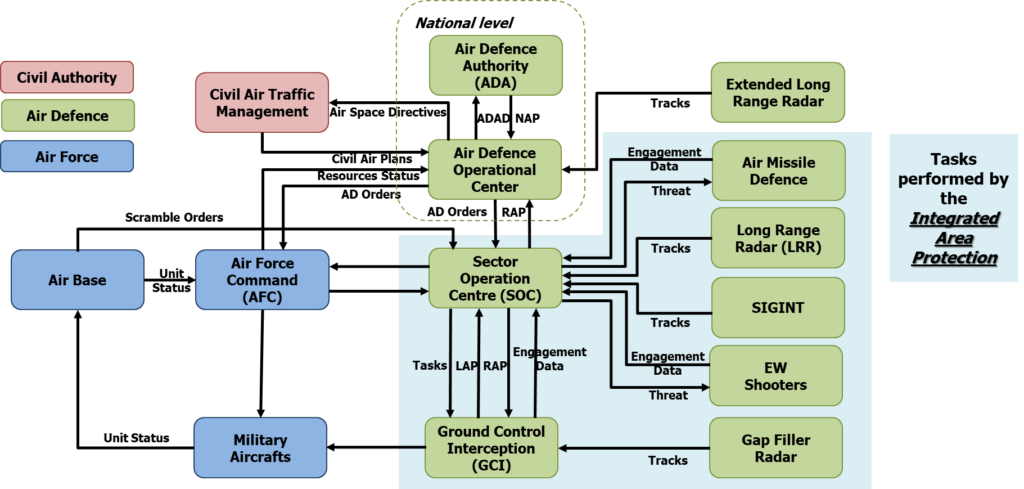
Figure 2: Integrated area Protection as a brick of National Air Defence
The Architecture of the Integrated Area protection Systems must be sufficiently flexible to allow easy addition or removal of different types of sensors and effectors in a plug and play basis with a simple software re-configuration process.
This architecture is based on standard communication protocols although being sufficiently robust in front of possible Cyber-Attacks.
Systems already in operation must be able to easily incorporating and integrating the fast technological evolutions of sensors and effectors to be upgraded and continuously adapted to the evolution of the threats, limiting also the obsolescence issues.







