Cyber Electro Magnetic Activities (CEMA)
Traditionally, Electronic Warfare (EW) and Cyber Warfare (CW) were considered as independent, disparate disciplines: Cyber-warriors worked at the bit level, while Spectrum-warriors operated below them, targeting Electro-Magnetic Spectrum (EMS).
However, as communications systems have moved to commodity hardware and as radar and navigation systems began to depend on networked operations using commodity network hardware, the boundaries between the two fields have begun to blur. Now, Cyber-warriors can provide effects that deny or degrade spectrum and Spectrum-warriors can create effects that allow for the control and exploitation of the network.
Traditionally, Electronic Warfare (EW) is any action involving the use of the electromagnetic spectrum (EMS) or directed energy to control the spectrum, attack an opponent, or impede opponent assaults via the spectrum: the ultimate purpose of EW is to deny the opponent the advantage of and ensure friendly unimpeded access to, the EMS.
On the other side, traditionally, Cyber Warfare (CW) involves the use and targeting of computers and networks in warfare to gain a military/economic/competitive advantage by gathering significant information from an enemy or interfering with the enemy’s ability to move information over the Internet or other networks or to process information within a computer.
Cyber Warfare involves both offensive and defensive operations pertaining to the threat of cyberattacks, espionage, and sabotages conducted by the use of malware, which is software whose purpose is to cause harm.
Both EW and CW aim to perform similar operational functions against the opponent, such as:
- Collect information from the opponent
- Interfere with the opponent’s operational capability in accessing/using its resources
- Cause the opponent systems to initiate undesired actions
- Protect friendly capability from opponent’s electronic interference
- The following table reports a comparison between EW and CW in terms of operational functions and how they are perpetrated versus the opponent, showing that each of the EW fields has a parallel technique in Cyber Warfare area.
|
Comparison of Electronic Warfare and Cyber Warfare Functions |
||
|
Operational Function |
Electronic Warfare |
Cyber Warfare |
|
Collect information from the opponent |
EW Support, which listens to enemy signals to determine enemy capabilities and operating mode |
Spyware, which causes information to be exported to a unwanted and hostile location |
|
Interfere with opponent’s operational capability |
Electronic Attack – JAMMING, which either covers received information or causes processing to give inaccurate outputs |
Viruses, which reduce available operating memory or modify programs to prevent proper processing outputs |
|
Cause opponent systems to initiate undesired actions |
Electronic Attack – DECEPTION (false targets), that look like credible targets, which are acquired and engaged by missiles or guns |
Trojan horses, which are hostile software accepted by enemy computers because they appear valid and beneficial |
|
Protect friendly capability from opponent’s electronic interference |
Electronic Protection, which prevents enemy jamming from impacting own operational capability |
Passwords and firewalls, which prevent malware from penetrating a computer |
The traditional difference between EW and CW is how the hostile function is introduced into an opponent’s systems.
EW enters the enemy systems’ functionality electromagnetically: through the Electronic Support functionalities, interception of signals transmitted by an opponent Spectrum Dependent System (a Radar system or a radio) is performed, while through the Electronic Attack functionalities the ability of such systems to access and use the EMS is degraded, negated or spoofed.
Traditional cyber-attacks assume the malware entering the victim’s computer via the network, a USB drive, or any other software-based support.
Modern systems (civil, national infrastructures, military) are today increasingly based on communication networks without fixed infrastructure, entering into the categorization of Spectrum Dependent Systems. On the other hand, they are based on the use of computing capability to elaborate data and information, manage their functionalities, and control their status. Following the definition by US DoD, a computing system is a system whose performed functionalities are mainly implemented and/or are enabled by means of programmable devices, which include DSP, FPGA, CPU, GPU, and moreover, in terms of physical components, memory devices, interfaces, operating systems and application logic.
Therefore, a computing system that makes use of wireless interface, provides a vulnerability that can be exploited in order to:
- collect sensitive information, which can be used for any operation within the network,
- force the access to the network, to take advantage of the services of the network itself,
- degrade the performance of the network, up to deny the whole service,
- degrade/modify the performance of one or more nodes of the network, by introducing a dedicated data stream and inserting/activating malicious code in the computing system.
For a number of years, military operations have used electro-magnetic attacks to disrupt enemy radars on the battlefield, but today the access and manipulation of the EMS and/or the data and information carried by EMS let us foresee many additional capabilities.In other words, EMS is an entryway for cyber. EW and CW are trying to accomplish similar tasks; they can be used in conjunction and thus may be viewed as two sides of the same coin, which is often indicated as Cyber EW or Cyber Electromagnetic Activity (CEMA).
Cyber and Electro-Magnetic Activities report a full description of the approaches and the functions that can be considered as CEMA: “all offensive, defensive and information activities that shape or exploit the electromagnetic environment and the enabling activities that support them”.
Starting from this definition, CEMA are considered as an “enabler” for the following cyber operations:
- Offensive Cyber Operations (OCO)
- Defensive Cyber Operations (DCO) (Including Active Defence)
- Cyber Intelligence, Surveillance And Reconnaissance (Cyber ISR)
- Cyber Operational Preparation Of The Environment (Cyber OPE)
Currently, CEMA have been defined only within the EMSO vision, requiring strict coordination with the SIGINT unit for the cyber-surveillance and intelligence functions. Known activities seem confined to the interception of satellite or mobile communications, including inline decryption capabilities or downgrade and side-channel attacks which in turn imply an active interaction with the communication endpoints, going beyond the usual COMINT domain. This kind of function can be called “eavesdropping”, as defined for the cyber activities, and is used to obtain access to the content of the communications between the sub-systems working in an interconnected network.
In our classification, CEMA functions should be extended including the endpoints of wireless communication, i.e. the equipment used to establish the radio bearer and maintain it according to the physical and logical conditions of the medium.
This “conceptual extension” is needed to introduce the following functions:
- Disrupt the integrity of a wireless communication between two endpoints (using a Man-In-The-Middle or MITM attack).
- Attack the availability of a wireless communication, i.e. interrupt, permanently or for a period of time, the possibility of two endpoints to communicate, so generating functional effects on the performance of the target.
- Abusive binding, i.e. the capability to join a closed wireless network as a trusted node bypassing all the binding security countermeasures (spoofing, hijacking, etc.) or to access out-of-band side channels used for maintenance or other purposes.
- Wireless Endpoint exploitation, i.e. the possibility of interfering with the underlying endpoint’s communication control software and the remote execution of wanted behaviors, so gaining full or partial access to the resources and the capabilities of the endpoint.
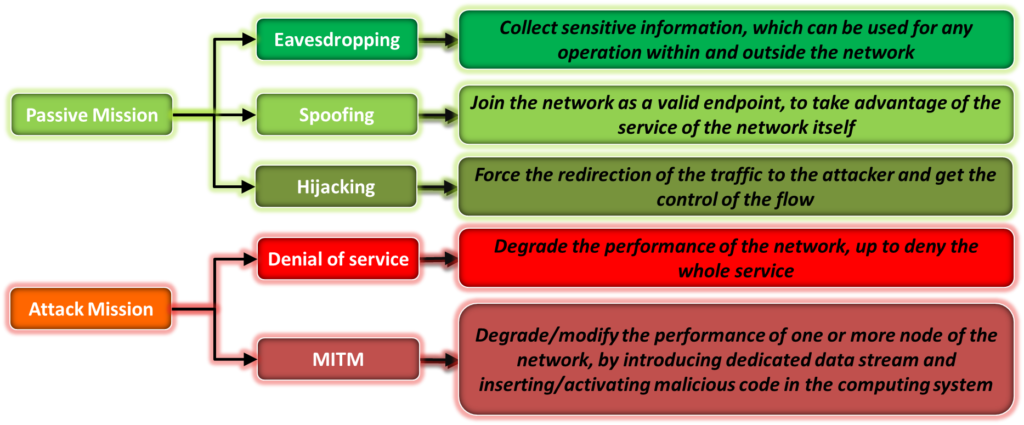
Figure 1: CEMA operations
The eavesdropping function is an entry point for further actions that can impact the computers connected to the network, or other bridged wireless communications, such as exfiltration of content.
This means that CEMA can be also considered as a “chain of activities” that combine endpoint wireless attacks with cyber-attacks to the exposed services, with the purpose of creating an impact inside one or more selected internal sub-systems, and obtain the needed operational advantage.
CEMA, therefore, fit into the concept of kill-chains, i.e. the sequence of attack tactics and techniques typically followed by an attacker to abuse a complex system.
The “Tactics, techniques and procedures” (TTPs) model is well known in the cyber intelligence world and more generally in the military domain. It has been created to identify how threat agents orchestrate and manage attacks against a specific target.
Tactics represent the reason “why” a specific technique is used inside a kill-chain.
Techniques instead represent the “how” an adversary can achieve the related tactical objective. Finally, procedures are strictly tight to techniques because they represent the specific implementation that an adversary adopts to obtain the desired result of the technique.
A given procedure is the “tool” used to execute the technique, it characterizes the adversary in a specific attack campaign and is usually used to extract a “signature” that can be deployed inside the detection countermeasures.
In the cybersecurity world, this signature is called IoC (Indicator of Compromise) and is used by all the active security devices to identify the action and neutralize it in real-time.
CEMA are or can be based on an operational cycle that requires multiple steps that need to be followed to identify it and that can be resumed in the following sequence:
- Intelligence & Analysis
- Mission Preparation
- Mission Execution
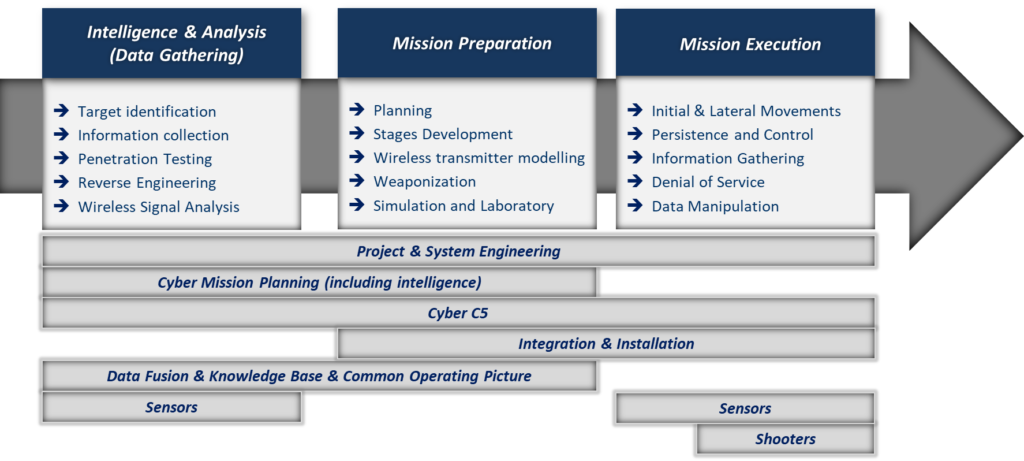
Figure 2: Operational cycle of CEMA
CEMA in offensive cyber activities (OCO) project power and a wide range of effects into the adversary’s network through the combination of EM and cyberspace activities.
The key focus of CEMA in OCO is on the cyber and EM capabilities of the adversary, on the detailed collection of all the technical aspects of the employed asset, and on the automated countermeasures and respond procedures.
To design such an operation requires long planning and it heavily focuses on the preparation steps and on the “lifecycle” of the operation. An early approach to CEMA was to acquire vulnerabilities, develop agents and launchers for every situation and finally continuously test the effective capability overtime to maintain the efficiency of the tools, waiting for the time to deploy them.
A second approach focuses on massive owning, i.e. the injection of control agents in adversary assets independently from their engagement or their criticality with respect to their operations, creating an army of insiders ready to be activated to support the OCO when needed.
A more effective strategy revolves again around the TTPs model It identifies effective kill-chains in terms of employment and not of technicalities. In this respect, an OCO’s kill-chain is defined in terms of the techniques and tactics that are engaged to obtain the desired effect. These include components, procedures, and all the elements that support the technique. Examples are post-exploitation chains, shellcodes, multi-stage and multi-vector strategies, protocol vulnerabilities, as well as those elements that can be reused because their functionalities can be easily re-packaged for the specific employment, like command and control platforms, RAT (Remote Access Trojan) or persistent launchers.
The kill-chain or chains judged most suitable will be weaponized only when the entire operation has been thoroughly defined.
Defensive Cyber Operations (DCO) are conceived, organized and conducted to defend cyberspace and to preserve the ability to utilize the EM. With respect to traditional cyber defensive strategies, the inclusion of the EM is pivotal, operationally and from a technological point of view.
This definition is strictly linked to the “cyber resilience” concept: “an entity’s ability to continuously deliver the intended outcome, despite adverse cyber events”. This means that a system maintains its resiliency if it maintains the desired performances.
As for OCO, also in the case of DCO, preparation is key to design and assess the maturity of the system resiliency with respect to CEMA. A specific type of assessment is based on the Cyber Resilience Review (CRR) created by the US Department of Homeland Security. Another one was introduced by Symantec Corporation and follows the NIST framework: Prepare/Identify, Protect, Detect, Respond, and Recover.
This intelligence activity must address the full picture of the adversary’s approach to a CEMA attack, which means:
- the knowledge of the adversary’s tools and capabilities
- the knowledge of the usual sequence of actions that characterize his approach to the attack, that can be described again using the TTP model
Once gathered the full knowledge of the adversary, DCO must map the adversary’s TTP scheme to the existing network elements in order to plan an effective enforcement strategy, so identifying the best applicable resiliency techniques. To automate this task we are adopting a modeling & simulation-based approach.








