Radar Electronic Counter Measures Techniques
Electronic countermeasures are used effectively to protect platforms such as aircraft and naval vessels.
RECM systems can work in different ways, for example creating electronically false targets, or blinding the platform to be protected from the view of enemy radars.
A possible classification of electromagnetic actions (Electronic Counter Measures) can be defined according to their main peculiarity:
-
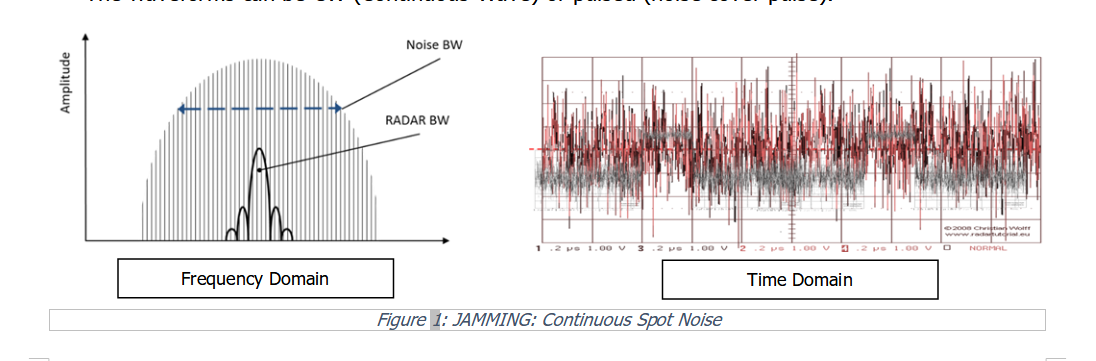
Jamming: These techniques are non-coherent and based on noise Frequency Modulation (FM) of the carrier.
The jamming waveform is created by a random electronic noise that modulates the carrier in order to appear at the Radar receiver as background noise to masking the desired radar echo.
The jamming waveforms can be matched to the radar BW (Spot Noise) or with a very wide bandwidth (Barrage Noise, often applied to counter frequency agile radars).
An additional sweeping modulation (with triangular, sawtooth, Gaussian law) in the frequency domain can be superimposed.
The waveforms can be CW (Continuous Wave) or pulsed (noise cover pulse).
Deception: The deception action consists in the transmission of signal as similar as possible to the original source.
These techniques are mainly coherent and based on the reception and re-transmission of the signal coming from the radar with additional modulations (frequency, time) superimposed (they are DRFM based).
The resultant waveform is coherent and naturally matched with the radar receiver that will not be able to discriminate it from the real echo.
Its intensity must be sufficient to overwhelm the transceiver and to “deceive” the receiver for synchronizing with the “false” transmitter with no evidence of the replacement, at waveform level.
In addition, cases of non-coherent deception techniques are contemplated (such as spoofing); in these cases, the replica of the received signal made by the DRFM is replaced by the direct synthesis of the carrier frequency of the jamming/deception signal.
Figure 1: JAMMING: Continuous Spot Noise
The effectiveness of the RECM depends on several factors:
• Distance (range) from the victim Radar: affected parameters:
◦ J/S, power relationship between jammer and echo: radar echo, at the radar receiver, will have a two-way propagation while the jammer will have a one-way propagation.
This means:
▪ a very big advantage in case of SIJ and some cases of EJ (the jammer is very closer with respect to the echo);
▪ an advantage in case of SPS and EJ (the jammer is almost at the same distance than the echo);
▪ a disadvantage in case of SOJ (the jammer is very far with respect to the echo);
◦ Same geometrical considerations apply to time domain:
▪ when the jammer is closer to the radar with respect to the defended platform/platforms (SIJ and some cases of EJ) totally coherent (follower) techniques can be applied (the jammer is able to receive, manipulate and re-transmit the signal before the arrival of the echo);
▪ when the jammer at the same distance from the radar with respect to the defended platform/platforms (SPJ and most of the cases of EJ) totally coherent (follower) techniques can be applied only for certain categories of radars (fixed frequency radars or agile radars with large PW’s), noise non-coherent techniques are applied in all the other cases ;
▪ when the jammer is at a longer distance from the radar with respect to the defended platform/platforms (SOJ) noise non-coherent techniques are applied;
• Level of the generated signal (affected parameter: J/S).
• Stealth capability of the defended platform/platforms: this will affect the RCS or Radar Cross Section and consequently the strength of the radar echo (affected parameter: J/S).
• Geographical constraints (obstacles, terrain);
• Duration of the service under threat;
• Intrinsic Electronic Protection measures of the attacked Radars.
To know more about this topic please read the following entries:






